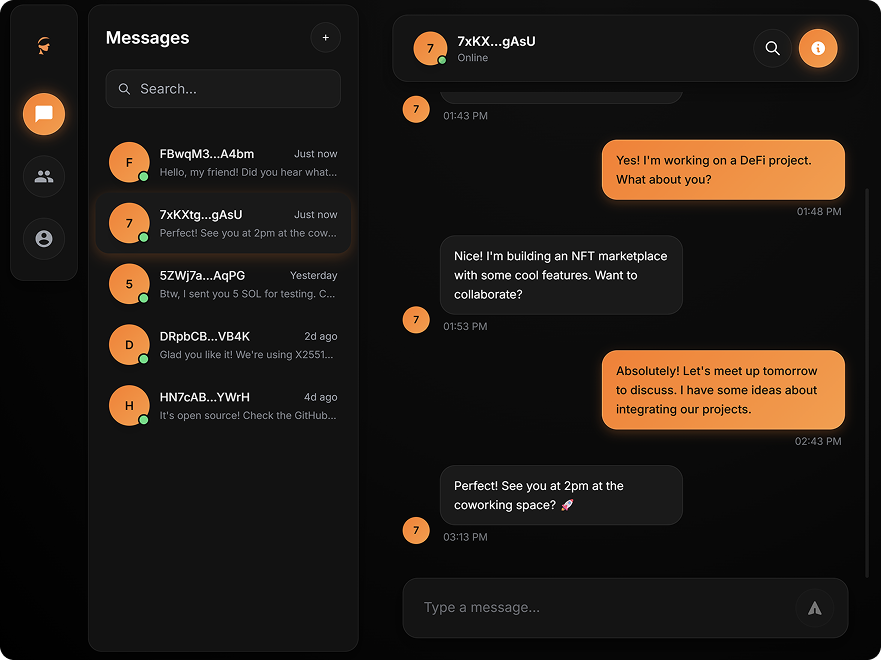
Servers shouldn't be trusted. They should be irrelevant.
Most apps ask you to trust their infrastructure. We don't. Your messages are encrypted on your device and stay encrypted everywhere else.
Private by design - not by policy.
We don't rely on "we promise we won't read your messages." We build it so we can't.
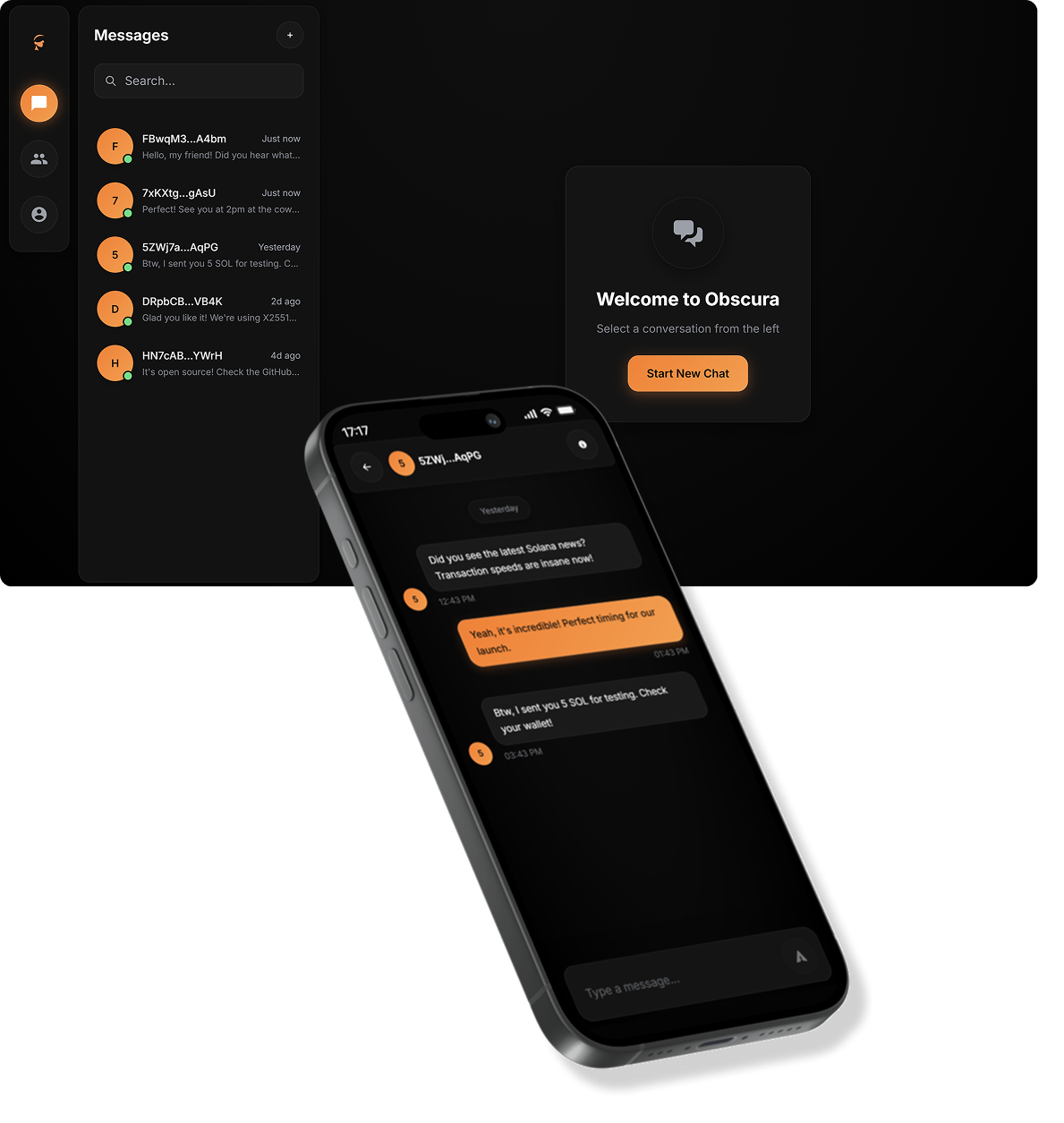
Servers shouldn't be trusted. They should be irrelevant.
Most apps ask you to trust their infrastructure. We don't. Your messages are encrypted on your device and stay encrypted everywhere else.
Private by design - not by policy.
We don't rely on "we promise we won't read your messages." We build it so we can't.
Simple flow. Serious cryptography.
You connect your wallet, your device creates a messaging key,
and every message is encrypted before it leaves your screen.
Our backend only delivers encrypted blobs — it never sees plaintext.

Connect Phantom
Your wallet becomes your identity. No phone number. No email. No accounts to leak.

Create your messaging key (on-device)
On first use, your device generates a dedicated messaging encryption keypair. The public key is linked to your wallet address. The private key stays on your device and is never uploaded.

Encrypt → Send
When you send a message, your client encrypts it locally using the recipient's public key. Only encrypted blobs leave your device — unreadable to everyone except the intended recipient.

Receive → Decrypt
When a message arrives, your device decrypts it locally using your private key. Only you can open it — not us, not our servers, not any third party.
Simple flow. Serious cryptography.
You connect your wallet, your device creates a messaging key, and every message is encrypted before it leaves your screen. Our backend only delivers encrypted blobs — it never sees plaintext.

Connect Phantom
Your wallet becomes your identity. No phone number. No email. No accounts to leak.

Create your messaging key (on-device)
On first use, your device generates a dedicated messaging encryption keypair. The public key is linked to your wallet address. The private key stays on your device and is never uploaded.

Encrypt → Send
When you send a message, your client encrypts it locally using the recipient's public key. Only encrypted blobs leave your device — unreadable to everyone except the intended recipient.

Receive → Decrypt
When a message arrives, your device decrypts it locally using your private key. Only you can open it — not us, not our servers, not any third party.
Compare it
Others
- •Encrypt, but often rely on servers and closed infrastructure.
- •Store encrypted content, but still operate as a central point of failure.
- •Phone numbers, emails, or app-specific accounts.
- •Password resets, SIM-based accounts, or platform logins.
- •Verification is often tied to phone numbers or proprietary identity systems.
- •Limited integration with on-chain identity and permissions.
- •Breaches still expose metadata and sometimes sensitive account.



Compare it
Others
- •Encrypt, but often rely on servers and closed infrastructure.
- •Store encrypted content, but still operate as a central point of failure.
- •Phone numbers, emails, or app-specific accounts.
- •Password resets, SIM-based accounts, or platform logins.
- •Verification is often tied to phone numbers or proprietary identity systems.
- •Limited integration with on-chain identity and permissions.
- •Breaches still expose metadata and sometimes sensitive account.




Choose your privacy level
Choose your privacy level
Same product. Same UI.
Different privacy guarantees - chosen by you.
Same product. Same UI.
Different privacy guarantees - chosen by you.
FAQ
FAQ
1. Can you read my messages?
No. Messages are encrypted on your device and only decrypted on the recipient's device. Our backend stores ciphertext blobs—unreadable data without your private messaging key.
2. Do I need an account or phone number?
3. Does the recipient need to be online for me to send a message?
4. What do you store on the server then?
5. What happens if I lose my device— do I lose access to messages?